One of the tools a router uses to decide where a packet should go is a configuration table. A configuration table is a collection of information, including:
As the number of routers and networks grows, the complexity of the overall network topology
increases.
For now its important to realize that network routing occurs via packet switching.
In this system, the data in a message or file is broken up into packages about 1,500 bytes long.
Each of these packages gets a wrapper that includes information on the sender's address,
the receiver's address, the package's place in the entire message,
and how the receiving computer can be sure that the package arrived intact.
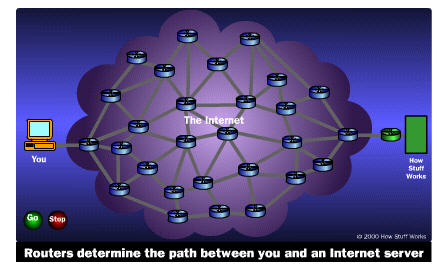
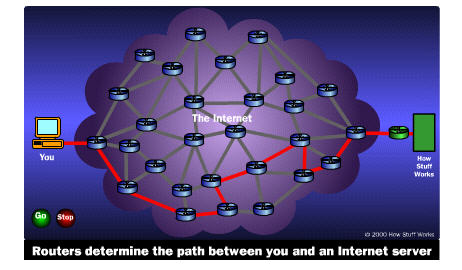
To help visualize this, consider the following situation:
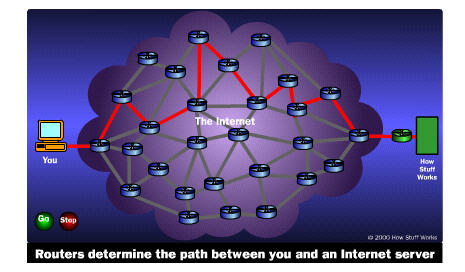
Route of second packer
There are two huge advantages to designing this kind of switched information network:
None of this can work well, without a good set of reliable protocols. One of the crucial tasks for any router is knowing when a packet of information stays on its local network. Again this is the primary funciton of the subnet mask. The subnet mask looks like an IP address and usually reads "255.255.255.0." This tells the router that all messages with the sender and receiver having an address sharing the first three groups of numbers are on the same network, and shouldn't be sent out to another network. In the early days of campus networking (e.g. 1987-1992), when various yahoos were trying to configure their own routes and networks, coding in the wrong sub net mask was a common error. If you misidentify your subnet mask, then your machine doesn't really understand what LAN its really on within the overall campus network and this misidentification lead to total network dysfunctionality. |