
In the earlier days of the internet, routers with relatively slow processors could get easily overloaded and clogged. Even today, that sometimes happens.
Its probably best to view a router as a device that exchanges messages (packets) with other networks - i.e. those beyond your LAN.
Today, and for quite some time, packet flow through routers and on networks has been governed by Ethernet and its rules (see more below). The current state of ethernet has the following one very important attribute:
While these attribute keeps packet routing somewhat simple, this architechture necessarily leads to performance consequences if networks are too large. As a result its desirable to set up multiple networks (often can subnets) within an overall large company or campus. For instance, the UO has about 100 subnets within its domain and each subnet subnets has its own router.
For example:

The network address of the machine bigmoo.uoregon.edu is 128.223.21.200
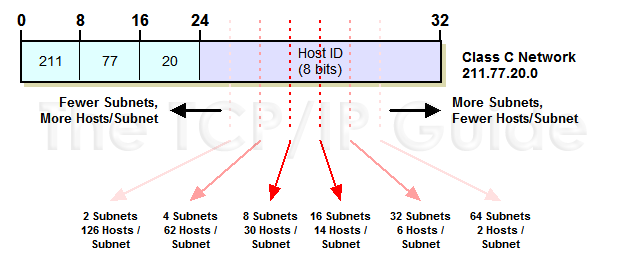
In this implementation of network addressing, IPv4, there are only 8 bits (e.g. 255 numbers)
available per field. Thus, suppose that the Knight Library has more than 255 machines that
it wants to network  well then a new subnet will have to be created
which really means acquiring another router.
well then a new subnet will have to be created
which really means acquiring another router.
*But this is a simplification; in reality its possible to create different subnet masks to aggregregate a number of separate 255 node channels onto a single subnet. We won't got into this in detail, but the generic concept of the subnet mask in IP routing basically tells the router how big their LAN is and what address space efines that LAN. Any address not in that space is then another network.
For instance, in the Knight library 128.223.84.xxx, 128.223.85.xxx, 128.223.86.xxx and 128.223.87.xxx are all on the same subnet. Thus, in this case, 1000 machines could go on the same subnet.
Subnetting this then a mechanism for managing the growing complexity of your network and offers you flexibility between maximzing hosts per subnet, or maximizing number of subnets. This is all controlled through the subnet mask.
One of the tools a router uses to decide where a packet should go is a configuration table. A configuration table is a collection of information, including:
A router, then, has two separate but related jobs:
As the number of networks attached to one another grows, the configuration table for handling traffic among them grows, and the processing power of the router is increased. This is where most of the current expense in terms of hardware is, for large routers.
The UO border router, the interface between uoregon.edu and the global internet, is a box that costs on order of 100K.
The Packet Switching Network.
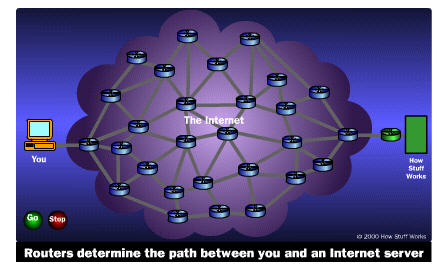
As the number of routers and networks grows, the complexity of the overall network topology
increases. This can lead to chaotic routing, a subject we will get into during the very
end of this course.
For now its important to realize that network routing occurs via packet switching. In this system, the data in a message or file is broken up into packages about 1,500 bytes long. Each of these packages gets a wrapper that includes information on the sender's address, the receiver's address, the package's place in the entire message, and how the receiving computer can be sure that the package arrived intact.
In this system, the data in a message or file is broken up into packages about 1,500 bytes long. Each of these packages gets a wrapper that includes information on the sender's address, the receiver's address, the package's place in the entire message, and how the receiving computer can be sure that the package arrived intact
To help visualize this, consider the following situation:
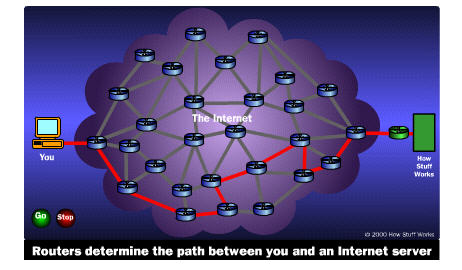
Route of second packer
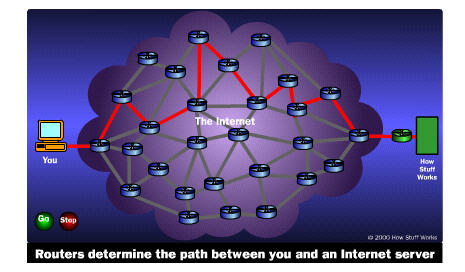
There are two huge advantages to designing this kind of switched information network:
One of the crucial tasks for any router is knowing when a packet of information stays on its local network. For this, it uses a mechanism called a subnet mask. The subnet mask looks like an IP address and usually reads "255.255.255.0."
This tells the router that all messages with the sender and receiver having an address sharing the first three groups of numbers are on the same network, and shouldn't be sent out to another network.
In the early days of campus networking (e.g. 1987-1992), when various yahoos were trying to configure their own
routes and networks, coding in the wrong sub net mask was a common error. If you misidentify
your subnet mask, then your machine doesn't really understand what LAN its really on within
the overall campus network  Not a good idea.
Not a good idea.